In the meantime, it is vital that you avoid logging in or making any changes to the files/folders on the account so the necessary timestamps stay in place for the investigation to proceed as smoothly as possible. The Security team will notify you via email reply once the investigation has been completed.
A sad reality about running websites is that sometimes they could get hacked. Having our WordPress site hacked a few times in the past, we know exactly how stressful it can be. Not to mention the impact it has on your business and readership. Over the past few years, we have helped hundreds of users recover their hacked WordPress sites including several well-known businesses. In this article, we will share a step by step guide to fixing your hacked WordPress site
Step 0 – Have a Professional Do it for You
Security is a serious matter, and if you’re not comfortable dealing with codes and servers, then it’s almost always better to have a professional do it.
Why? Because hackers hide their scripts in multiple locations allowing for hacks to come back over and over again.
Although we will show you how to find and remove them later in this article, a lot of folks want to have the peace of mind knowing an expert properly cleaned their website.
Security experts normally charge anywhere between $100 to $250 per hour which is outrageous for a small business or solo-entrepreneur.
However for WPBeginner readers, our friends over at Sucuri offer malware and hack cleanup for $199 which also includes their firewall and monitoring service for a whole year.
Now this may seem like a promotion of Sucuri, but it’s really an honest recommendation. We personally know the team at Sucuri, and we wouldn’t be recommending them if we didn’t trust them with our own websites. Yup WPBeginner uses Sucuri and on a daily basis they block several thousand attacks on our website, and we really can’t thank them enough for what they do for us.
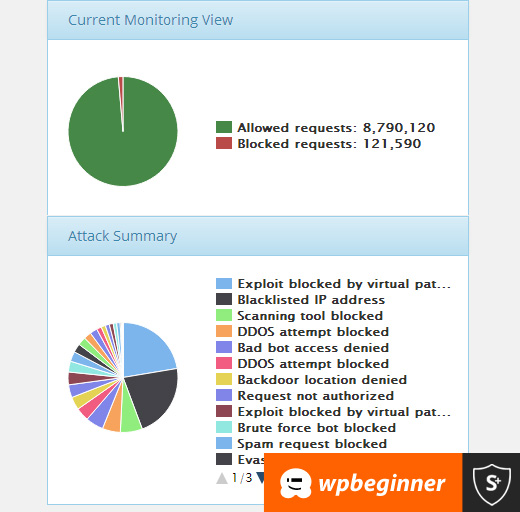
So use them if you value your time, you’re not tech-savvy, or if you just want peace of mind.
For all the DIY folks, simply follow the steps below to clean up your hacked WordPress site.
Step 1. Identify the Hack
When dealing with a website hack, you’re under a lot of stress. Try to remain calm and write down everything that you can about the hack.
Below is a good checklist to run down through:
- Can you login to your WordPress admin panel?
- Is your WordPress site redirecting to another website?
- Does your WordPress site contain illegitimate links?
- Is Google marking your website as insecure?
Write down the list because this will help you as you talk with your hosting company or even as you go down the steps below to fix your site.
Also it’s crucial that you change your passwords before you start the clean up. You will also need to change your passwords, when you’re done cleaning the hack.
Step 2. Check with your Hosting Company
Most good hosting providers are very helpful in these situations. The have experienced staff who deal with these kind of things on a daily basis, and they know their hosting environment which means they can guide you better. Start by contacting your web host and follow their instructions.
Sometimes the hack may have affected more than just your site, specially if you are on shared hosting. Your hosting provider may also be able to give you additional information about the hack such as how it originated, where the backdoor is hiding, etc. From our experience, HostGator and Siteground both are very helpful when something like this happens.
You may even get lucky and the host might clean up the hack for you.
Step 3. Restore from Backup
If you have backups for your WordPress site, then it may be best to restore from an earlier point when the site wasn’t hacked. If you can do this, then you’re golden.
However if you have a blog with daily content, then you risk losing blog posts, new comments, etc. In those cases, weigh the pros and cons.
Worst case, if you don’t have a backup, or your website had been hacked for a long time, and you don’t want to lose the content, then you can manually remove the hack.
Step 4. Malware Scanning and Removal
Look at your WordPress site and delete any inactive WordPress themes and plugins. More often than not, this is where hackers hide their backdoor.
Backdoor is referred to a method of bypassing normal authentication and gaining the ability to remotely access the server while remaining undetected. Most smart hackers always upload the backdoor as the first thing. This allows them to regain access even after you find and remove the exploited plugin.
Once you have done that, now go ahead and scan your website for the hacks.
You should install the following free plugins on your website: Sucuri WordPress Auditing and Theme Authenticity Checker (TAC).
When you set these up, the Sucuri scanner will tell you the integrity status of all your core WordPress files. In other words, it shows you where the hack is hiding.
The most common places are themes and plugin directories, uploads directory, wp-config.php, wp-includes directory, and .htaccess file.
Next run the Theme Authenticity Checker, and it will display your results like this:
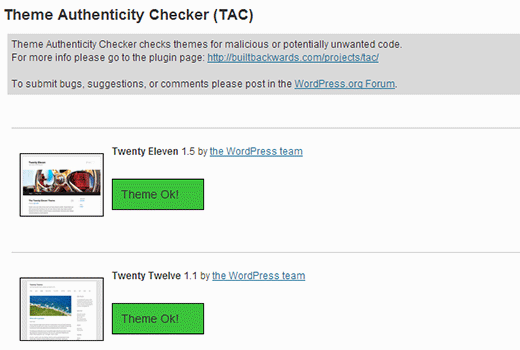
If theme authenticity checker finds any suspicious or malicious code in your themes, it will show a details button next to the theme with the reference to the theme file that is infected. It will also show you the malicious code it found.
You have two options for fixing the hack here. You can either manually remove the code, or you can replace that file with the original file.
For example, if they modified your core WordPress files, then re-upload brand new WordPress files from a fresh download or all WordPress files for that matter to override any affected files.
Same goes for your theme files. Download a fresh copy and override the corrupted files with the new ones. Remember do this only if you didn’t make changes in your WordPress theme codes otherwise you’ll lose those.
Repeat this step for any affected plugins as well.
You also want to make sure that your theme and plugin folder matches the original ones. Sometimes hackers add additional files that look like the plugin file name, and are easy to ignore such as: hell0.php, Adm1n.php etc.
We have a detailed guide on how to find a backdoor in WordPress and remove it.
Keep repeating this step until the hack is gone.
Step 5. Check User Permissions
Look in the users section of WordPress to make sure only you and your trusted team members have administrator access to the site.
If you see a suspicious user there, then delete them.
Read our beginner’s guide to WordPress user roles.
Step 6. Change Your Secret Keys
Since WordPress 3.1, WordPress generates a set of security keys which encrypts your passwords. Now if a user stole your password, and they are still logged into the site, then they will remain logged in because their cookies are valid. To disable the cookies, you have to create a new set of secret keys. You need to generate a new security key and add it in your wp-config.php file.
Step 7. Change Your Passwords AGAIN
Yes, you changed the passwords in step 1. Now do it again!
You need to update your WordPress password, cPanel / FTP / MySQL password, and basically anywhere else that you used this password.
We highly recommend that you use a strong password. Read our article on the best way to manage passwords.
If you have a lot of users on your site, then you may want to force a password reset for all of them.
Moving Forward – Hardening your WordPress site

It should go without saying that there is no better security than having a good backup solution in place. If you don’t have one, then please put something in place to backup your site daily.
Aside from that, here are some more things you can do to better protect your site – these are not in order and you should do as many as you can!
- Setup a Website Firewall and Monitoring System – Sucuri is the provider we use because in most cases they block the attacks before it reaches your server.
- Switch to Managed WordPress Hosting – Most managed WordPress hostingcompanies go to extra lengths to keeping your site secure. We recommend Pagely or WPEngine.
- Disable Theme and Plugin Editors – It’s a best practice. Here’s how to disable file edit in WordPress.
- Limit Login Attempts in WordPress – We recently covered the importance of it and you should read how to limit login attempts in WordPress.
- Password Protect your Admin Directory – Add an additional layer of password to your WordPress admin area. See how to add Htpasswd to WordPress admin.
- Disable PHP Execution in certain directories – Adds additional layer of security – here’s how to disable PHP execution via .htaccess.



